Ecuador's President Lenín Moreno faces party revolt
Ecuador's President Lenín Moreno has been removed from his post of leader of the governing Alianza País party by the party's national leadership committee.
Mr Moreno's position as the country's president is not affected but the committee said that Alianza País would now be led by the former foreign minister, Ricardo Patiño.
Supporters of Mr Moreno said they did not accept the committee's decision.
The move highlights the deep divisions inside the governing party.
Alianza Pais' leadership committee accused Mr Moreno of not following the party's political line.
Who is Lenin Moreno?
- 64 years old, left-wing, former vice-president
- Became paraplegic after being shot in the back during a robbery in 1998
- Wants to increase employment opportunities and give all Ecuadoreans the chance to go on to higher education
- Has written books with titles such as "Being Happy is Easy and Fun"
The move by the committee came after former party leader Rafael Correa called Mr Moreno a "traitor" to the "citizens' revolution" led by Mr Correa when he was president of Ecuador from 2007 to 2017.
The committee also called on Mr Correa to return from Belgium to "lead the restructuring of the Alianza País movement".
Mr Correa moved to Belgium, where his wife is from, after serving his third term in office.
The former president has been fiercely critical of his successor in office, who he has labelled a "wolf in sheep's clothing".
He has accused Mr Moreno, who served as Mr Correa's vice-president from 2007 to 2013, of pretending for years to be a close political ally only to change his political colours once he came to power.
Mr Moreno has struck a more conciliatory note with the country's opposition and has also backed investigations into alleged corruption during Mr Correa's administration.
The corruption probe has led to the arrest of Vice-President Jorge Glas, a close friend of Mr Correa.
While the decision by Alianza Pais's national committee to remove Mr Moreno from the party's top post was taken unanimously, the move has been met with criticism by other members of the party.
Ecuador's acting vice-president, María Alejandra Vicuña, called it "arbitrary".
The president of Ecuador's National Assembly, Jose Serrano, who is a fellow member of Alianza País, also expressed his support for Mr Moreno.
 Media playback is unsupported on your device
Media playback is unsupported on your device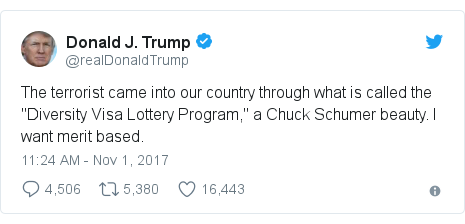 Image Copyright @realDonaldTrump @realDonaldTrump
Image Copyright @realDonaldTrump @realDonaldTrump 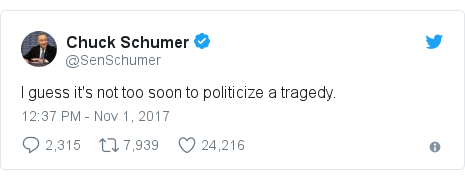 Image Copyright @SenSchumer @SenSchumer
Image Copyright @SenSchumer @SenSchumer  Media playback is unsupported on your device
Media playback is unsupported on your device